Review: Ubiquiti UniFi Security Gateway
Sometime after I reviewed the Ubiquiti EdgeRouter Lite, Ubiquiti contacted me and offered me a few products to test and review. One of the products they sent me was the UniFi Security Gateway. At the time, I set the box aside as it didn't have all the features of the EdgeRouter Lite. In January when my father was having trouble with his Internet, I put the USG into service. For that application, it was ideal as it integrated with the rest of the components and was simple to manage.
After the success of that install, I was kind of jealous and decided to purchase a USG and see what it would take to replace my EdgeRouter Lite; the UniFi team has done a lot of work on the controller (the GUI to manage the device) since I was originally sent the device. Replacing a router should not be rocket science. Unfortunately for me, my network is a little bit customized. Going from the EdgeRouter Lite, I had to move over the following:
- Dynamic DNS (for my external IP address)
- IPv6
- VLANs
- Firewall rules for the VLANs
- OpenVPN server
- Static DHCP entries
- Static DNS host entries
Some of this is available in the controller, some of it isn't.
The first step was to adopt the USG into my controller. I followed the instructions on how to integrate the USG into an existing network. Unfortunately, I was unable to adopt (meaning the controller can manage the device) the USG. I tried a few times with no success. Next I looked at an article that allows me to configure the USG to find the controller (instead of the controller finding it). I followed the SSH instructions and issued the commands:
mca-cli
set-inform http://ip-of-controller:8080/inform
This worked and I started getting somewhere. (After reading some more posts on Ubiquiti's extremely helpful forum, it appears that an old firmware may have had issues adopting and that upgrading the firmware before adopting may have helped.)
After the USG was adopted into the controller, I plugged in the WAN connection, rebooted the cable modem (so that it would pick up the new MAC address) and was able to connect to the Internet. If I had a simple network, I'd be done, but nothing is ever easy for me.
Next up was setting static DHCP entries. While the current controller doesn't let you assign DHCP entries until after a device has been seen, all my devices were online and showed up in the controller (I have UniFi switches which makes the controller populate with all devices it sees) using the addresses I had assigned from the EdgeRouter Lite. It was a simple matter of selecting each device, clicking the "Use fixed IP address" checkbox and clicking Apply. (Note there is a bug in the UI where the checkbox doesn't stay checked even after applying.)
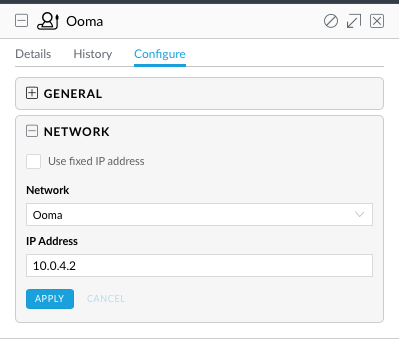
Perfect, so now that was out of the way (tedious, but reasonable), I could move on or so I thought. The controller lets me assign static IP addresses for clients; switches and access points are not considered clients. I needed static IP addresses for the switches and access points so that I could use SNMP monitoring on them; the package I'm using, Observium uses host names to address the devices; in order to use host names, I had to first give devices static IP addresses. This is where the messiness begins. Ubiquiti has an article on how to customize the USG and have the changes persist across reboots. (The EdgeRouter Lite just lets you configure it using the command line and the changes persist.)
You start the process by doing something like this:
configure
set service dhcp-server shared-network-name LAN_10.0.1.0-24 subnet 10.0.1.0/24 static-mapping UniFi-LR ip-address 10.0.1.131
commit
save
exit
and then
mca-ctrl -t dump-cfg
At this point, you have to pick through what was dumped and only choose what you entered manually as the json file you create gets merged in with what is produced from the controller. This isn't necessary if you have a standard config and the controller has all the options you need.
I then repeated this process for IPv6, static DNS entries and my OpenVPN server configuration.
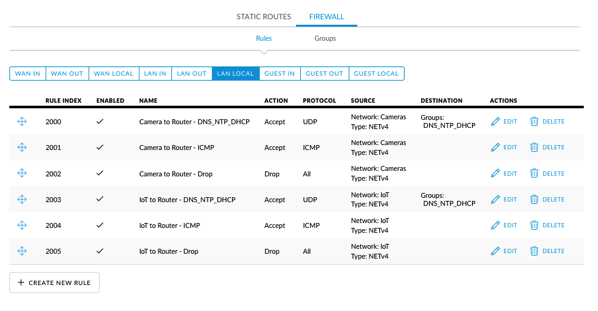
There is a GUI for configuring the firewall and I setup rules that prevent IoT devices from talking to my LAN, my cameras from talking to anything except 1 device, and a few other rules. This was straightforward, but a little different than on the EdgeRouter Lite.
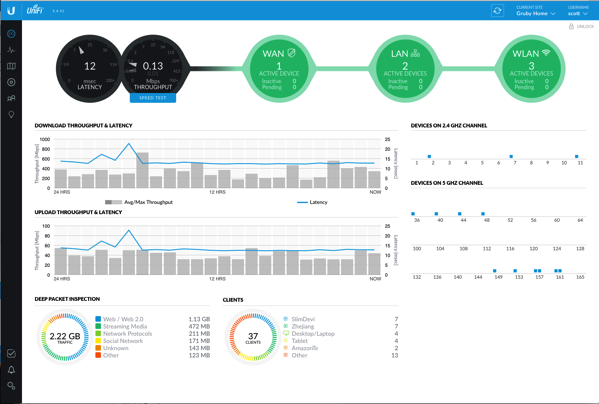
Now that I had the USG setup like my EdgeRouter Lite, what did I get? The hardware is virtually identical, so I didn't gain performance. The main thing I gained was being able to look at my entire network in 1 place. In addition, I get the ability to remotely manage/monitor my network through the UniFi cloud. Did I mention the pretty picture with the circles?
People are going to ask, why go with a USG over an EdgeRouter Lite. Here's my rundown:
USG
- Easily integrates with other UniFi equipment.
- Simplified configuration.
- Remote access via UniFi mobile app.
- Firewall configuration is slightly easier than on ERL, I think.
EdgeRouter Lite
- UI has some more advanced configurations like being able to change any option using the configuration tree.
- Firewall configuration in UI allows you to apply rules directly to VLANs.
- Configuration via command line is a one step process; make change and save it vs USG which has multiple steps.
- Core operating system is newer than USG.
- Static DHCP reservations can be made prior to a device being on the network.
Conclusion
Pros
- Easy setup for simple networks.
- Full view of entire network in one spot.
- Remote access to router from UniFi mobile app (using the UniFi cloud).
- Easy configuration of firewall entries.
Cons
- No IPv6 DPI (deep packet inspection).
- DPI works across all interfaces and may not give you an accurate representation of WAN traffic (which is what interests me).
- Not all configuration options are available via the GUI.
- Initial setup into a non-trivial existing network is painful.
- WAN speed test is only useful for up to 150 - 200 Mbps (according to a forum post; I have 300 Mbps down and can only get about 130 Mbps shown).
- JSON configuration for command line options is a bit awkward as you have to use the command line first, export the options and then pair down the result to put in the JSON config so that settings persist.
Summary
As I've written about in the past, the UniFi line of networking products is easy to use and everything works well together. The USG fits in well and despite my rough start with it, I'm pleased with it. While there wasn't a huge leap from the EdgeRouter Lite to the USG, being able to see my entire network configuration in one place makes it easier for me to manage. In the future, I plan on adding more firewall rules and possibly more VLANs to separate out more IoT traffic (a day doesn't go by where you don't here about some IoT device doing something shady).
If you already own an EdgeRouter Lite, moving to a USG is a tough decision. You gain no new functionality or performance, but an interface that works with other UniFi hardware. If you don't already own an EdgeRouter Lite and either plan on getting UniFi access points or switches, I think it is a no brainer to get a USG. If you aren't using other UniFi gear, a USG itself won't buy you a whole lot. With the USG, I'm able to define VLANs once and have it apply to the WiFi access points and the switch ports; with the EdgeRouter Lite, I had to define VLANs in both places for proper routing.
UniFi employees are quite active on their forums and have posted their roadmap. I really like some of the features and their openness is refreshing. The features won't really change how I use the device, but will help reduce the number of command line changes I have to make.