No, the title is not a typo. I’m coining the acronym Internet of Outdated Things! I’ve written in the past about keeping devices updated and the recent KRACK attack brings this issue back to the forefront. I’ve already updated by UniFi access points and am waiting for updates from Apple and Amazon for clients that I have connecting over WiFi. The only other devices that I have on my WiFi network are a few old SlimDevices Squeezeboxes.
These Squeezebox Radios are now over 5 years old, but still going strong. All our music in the house is streamed through 3 other Squeezebox devices that are hard wired, so I’m not concerned about those. Since Logitech stopped supporting these devices several years ago, I can’t realistically expect to get a firmware update to fix this WiFi issue. However, should I just toss the devices because I can’t get a firmware update? For some devices I’d take the opportunity to upgrade, but our music system has been running so well for so long that I’m not going to touch it. Where does that leave me? While the KRACK attack is mostly theoretical right now and the attacker must be in close proximity, I decided I had to figure out a way to mitigate this just for my own piece of mind.
I decided to start with the work I documented last year on blocking my IP cameras from talking to the Internet and modify it for this situation. This is a little different because I only want the Squeezebox devices talking to my Media Center running the Logitech Media Server and I want the devices to be able to talk to the Internet in order to stream music. Unlike last year, this exercise is all being done in the UniFi controller since I’m using a USG and UniFi access points.
So let’s begin:
- In the UniFi controller, go into Settings and select Networks.
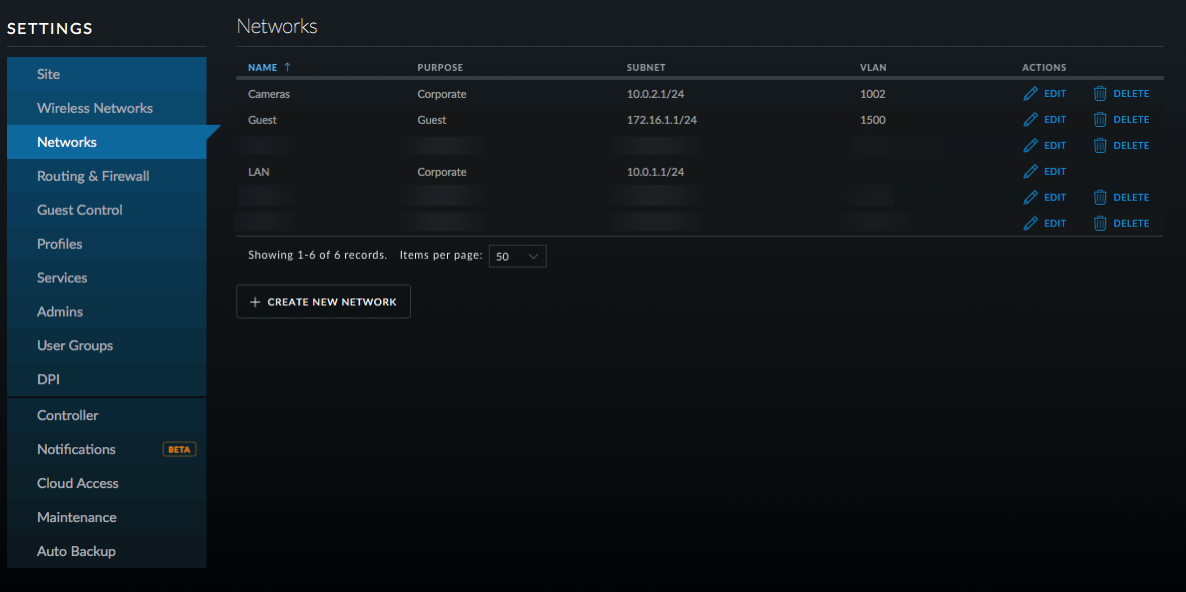
- Click on Create New Network.
- Enter a name for the network; I chose Music.
- Leave it on Corporate and LAN1.
- Enter a VLAN number; I chose 1006 and then enter the gateway as 10.0.6.1/24 or something similar depending on your network. Click on Update DHCP Range.
- You can enable DHCP guarding if you like so that only the USG is recognized as a DHCP server.
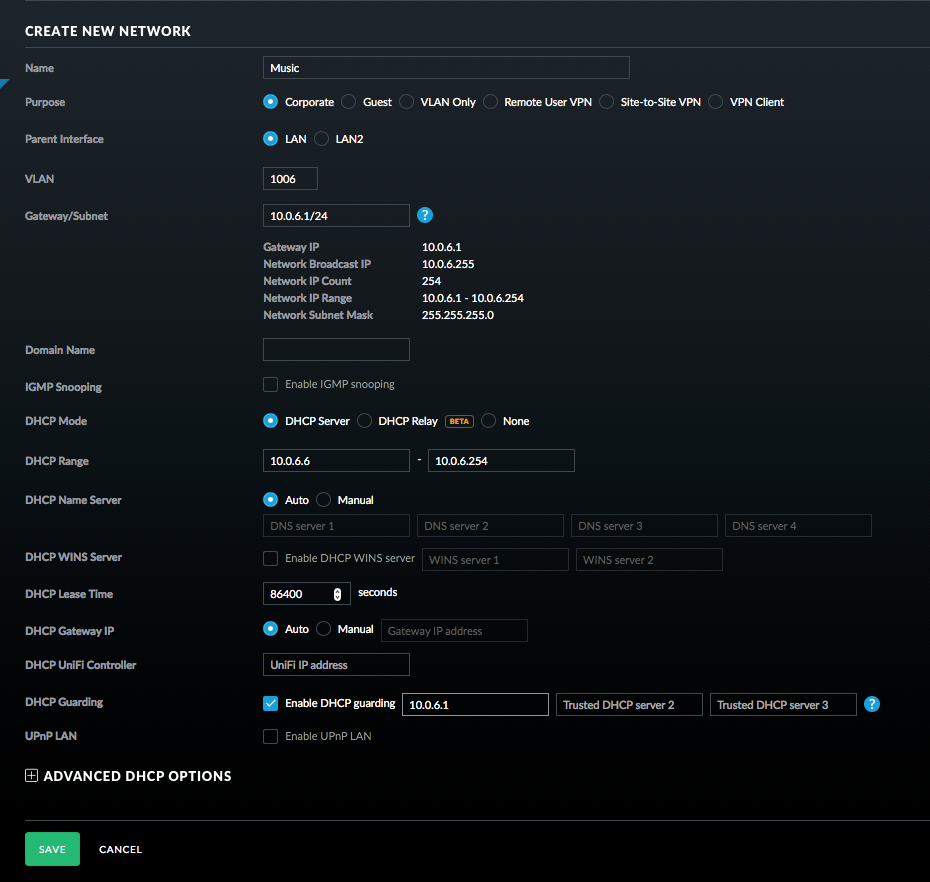
- Click Save.
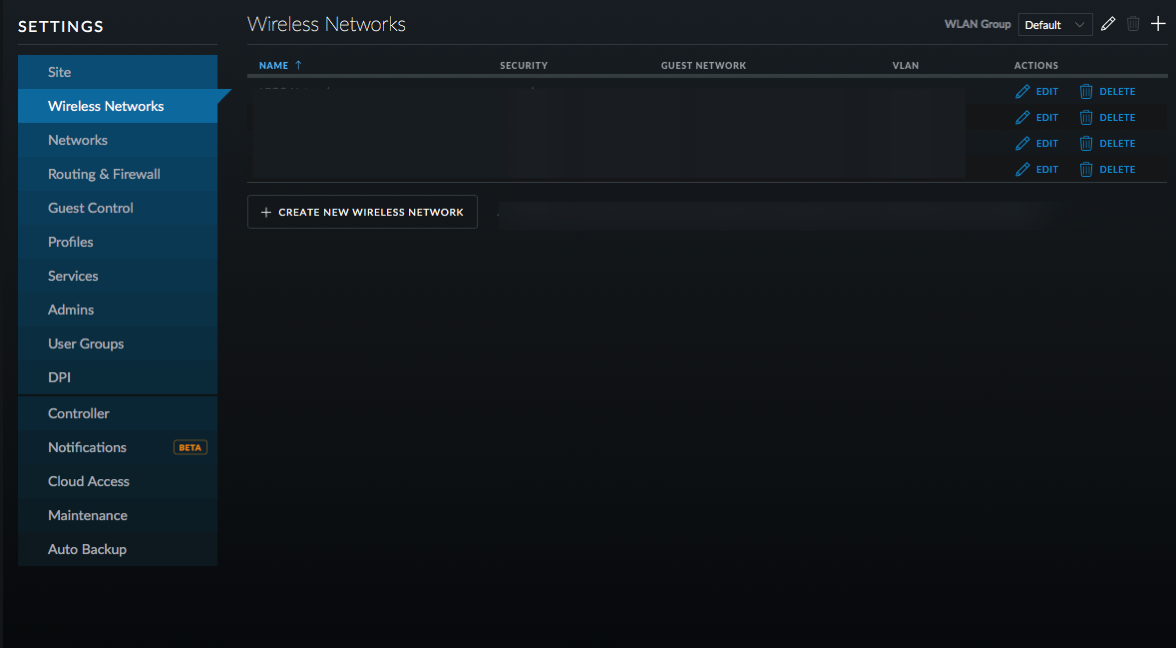
- Click on Wireless Networks and then Create New Wireless Network.
- Name the new network and turn on WPA Personal Security with a Security Key.
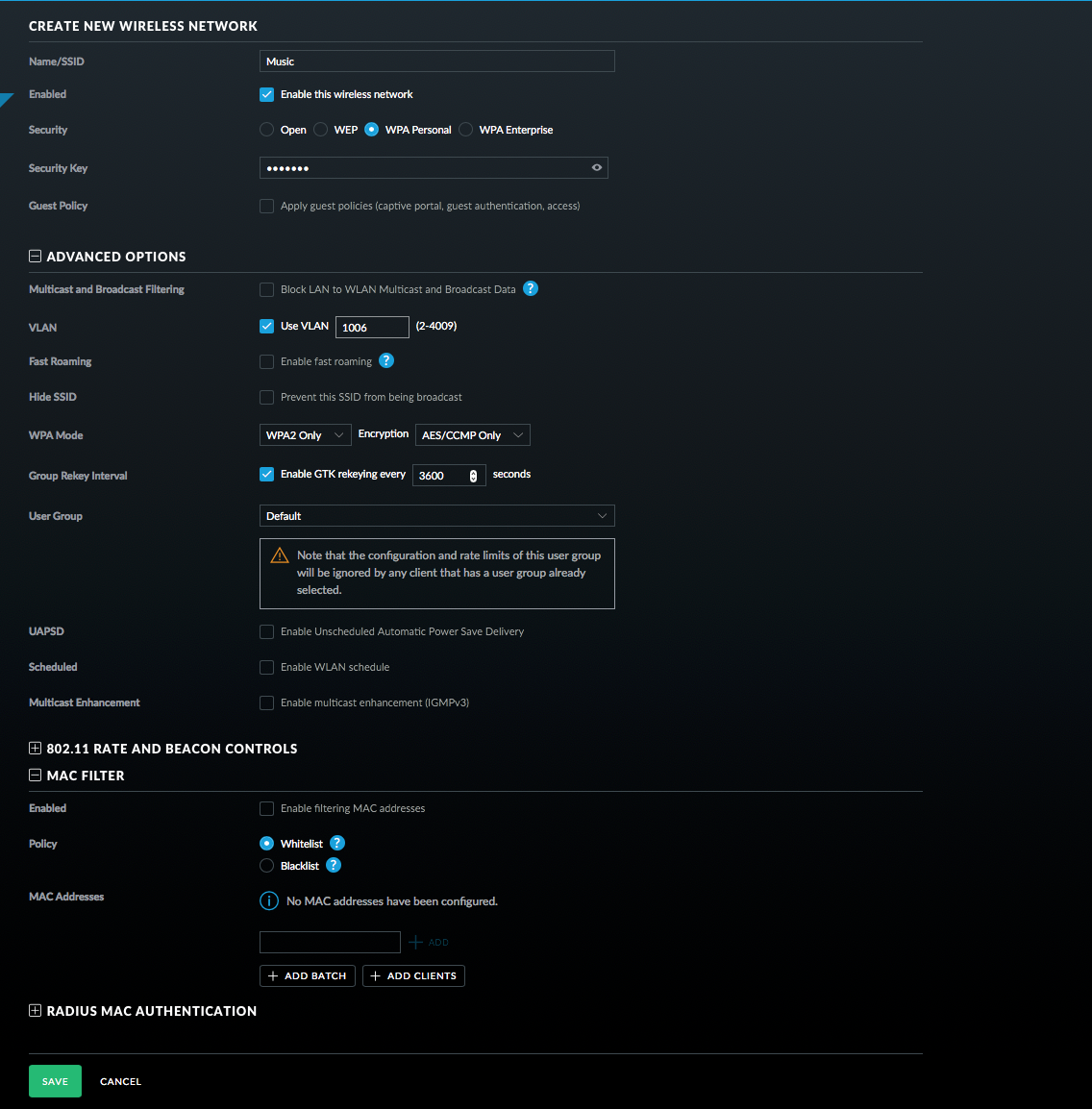
- Select Use VLAN and enter the VLAN you setup before.
- Click on Advanced Options and then on MAC Filter (note this may not be in all versions of the controller software).
- Whitelist your devices that you want to connect (this is not necessary and MAC addresses can be spoofed, but it can’t hurt).
- Click Save.
- Click on Routing & Firewall, Firewall, and then Select Groups. These groups will be used later in the firewall rules.
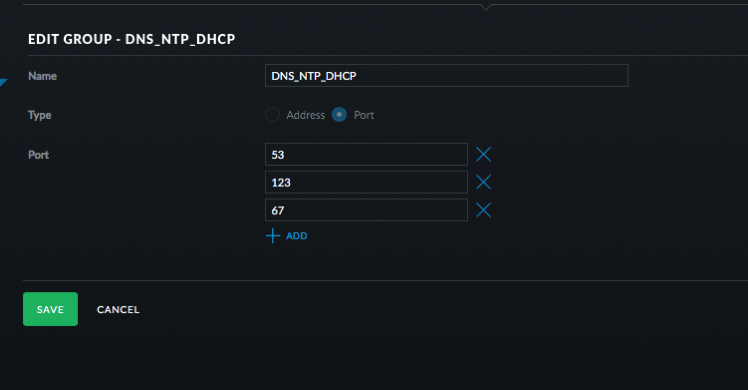
- Click Create New Group. Set it up as a Port group with 53, 123, and 67 as the ports. Name it DNS _ NTP _ DHCP.
- Click Save.
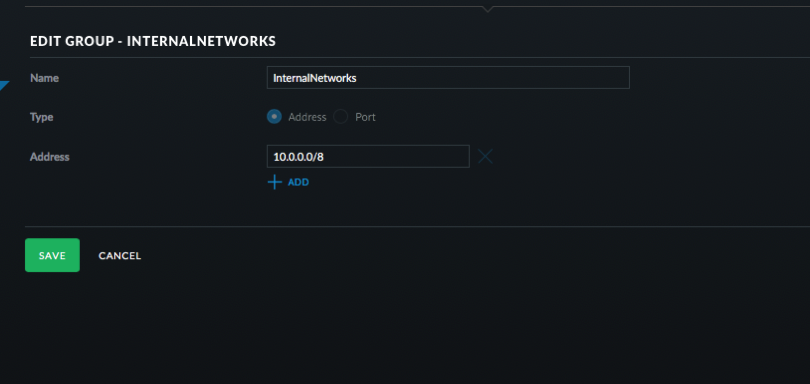
- Click Create New Group. Address group and use 10.0.0.0/8 and then click Save.
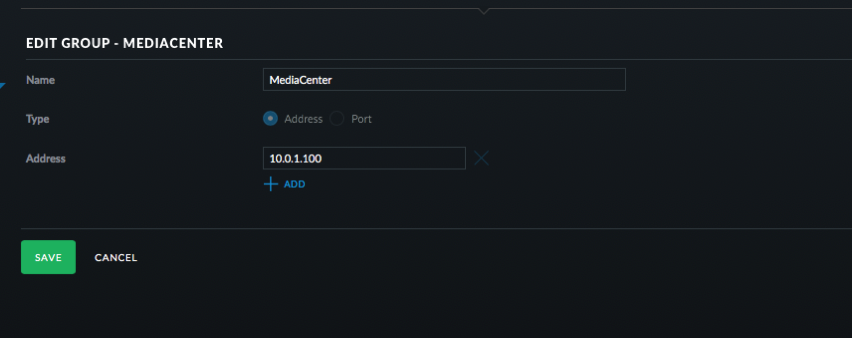
- Click Create New Group. Address group and use 10.0.1.100 or whatever is the address of your Logitech Music Server. Click Save.
- Click Create New Group. Port group and use 9090, 3483, and 900. Click Save.
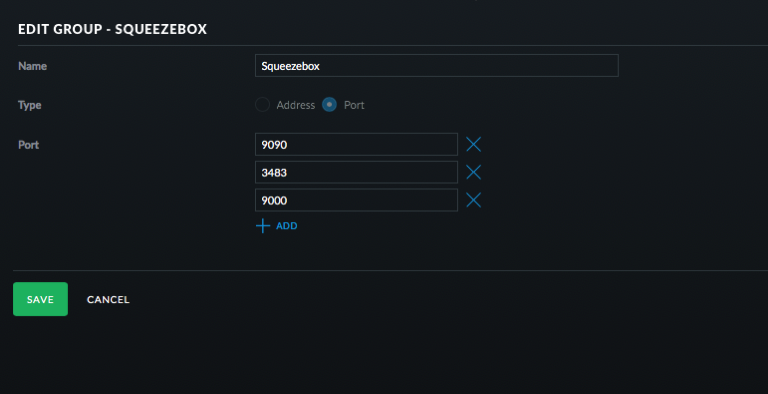
- Click on Rules and then LAN Local.
- Click Create New Rule.
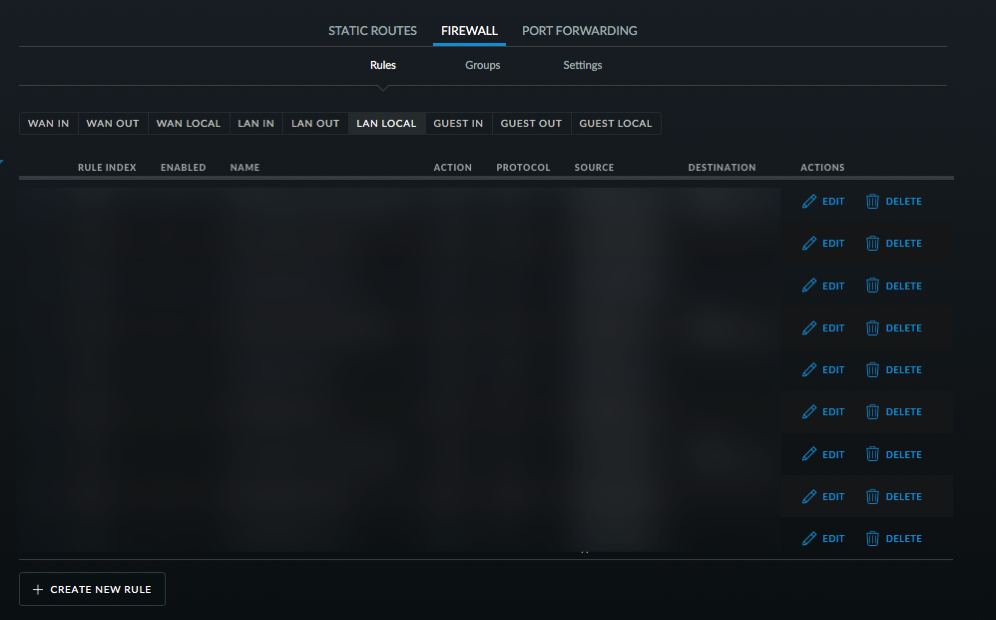
- Configure this rule to allow DNS, NTP, and DHCP requests from the Squeezebox devices to the router. Select UDP, New/Established/Related. Then select the Music Network and then the DNS _ NTP _DHCP port group as seen in the picture. Click Save.
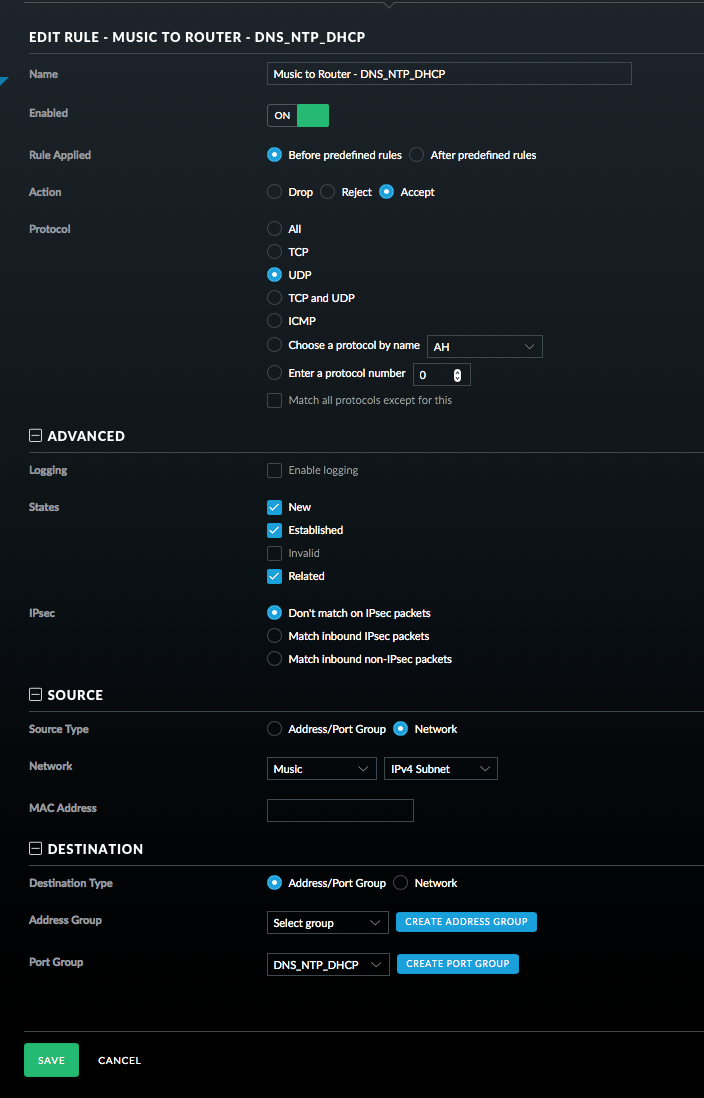
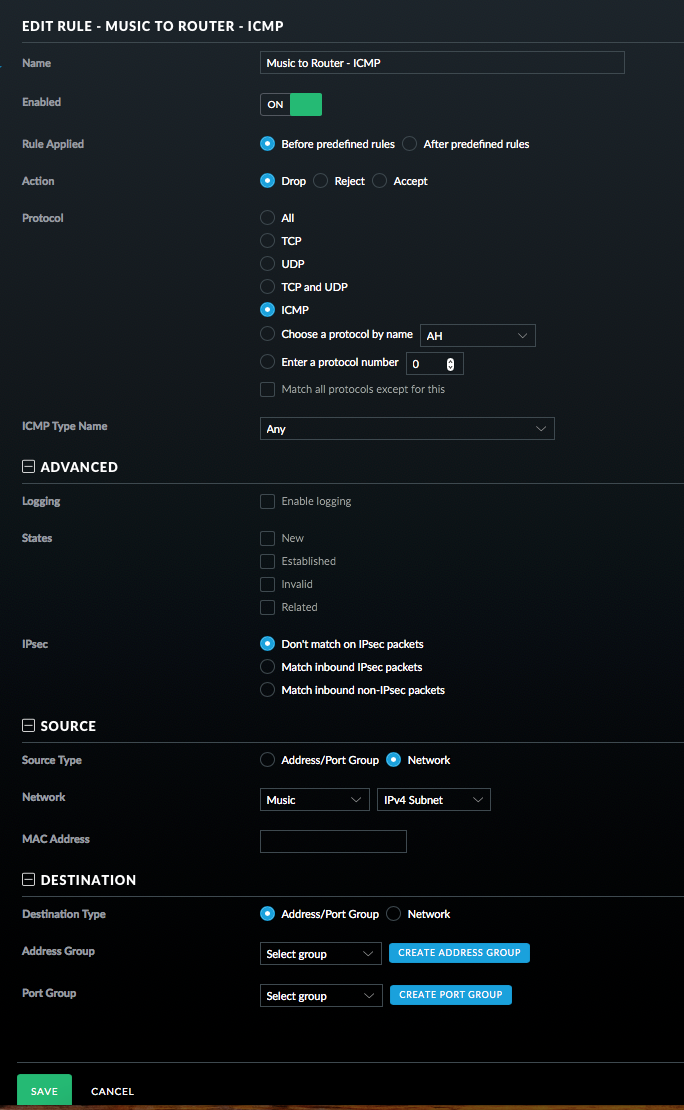
- Add a Rule for ICMP packets. See picture.
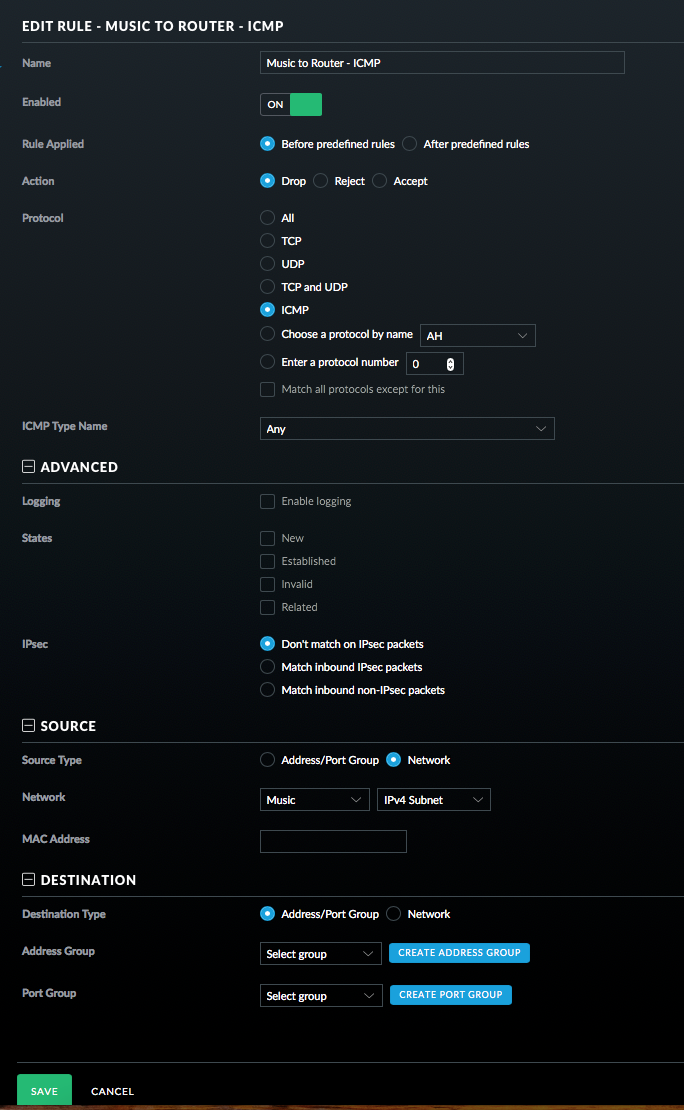
- Finally for this section, add a rule to drop all other traffic. This must be the last rule in this set.
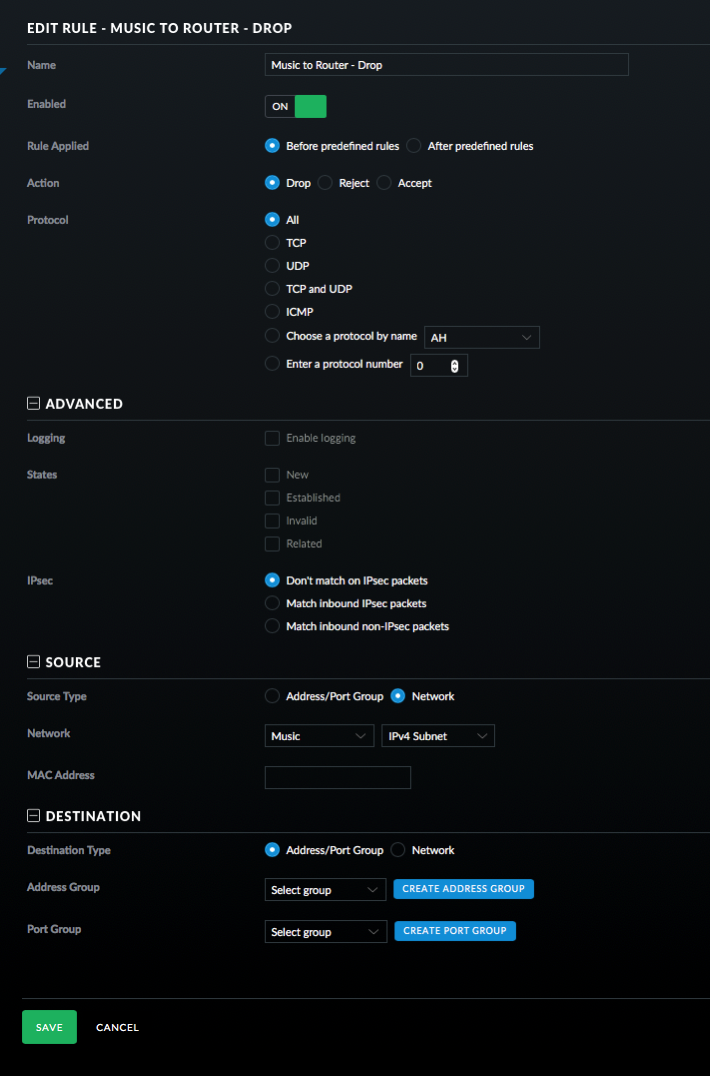
- Click on LAN IN and then Create New Rule.
- This rule allows traffic from the Squeezebox to the Media Center.
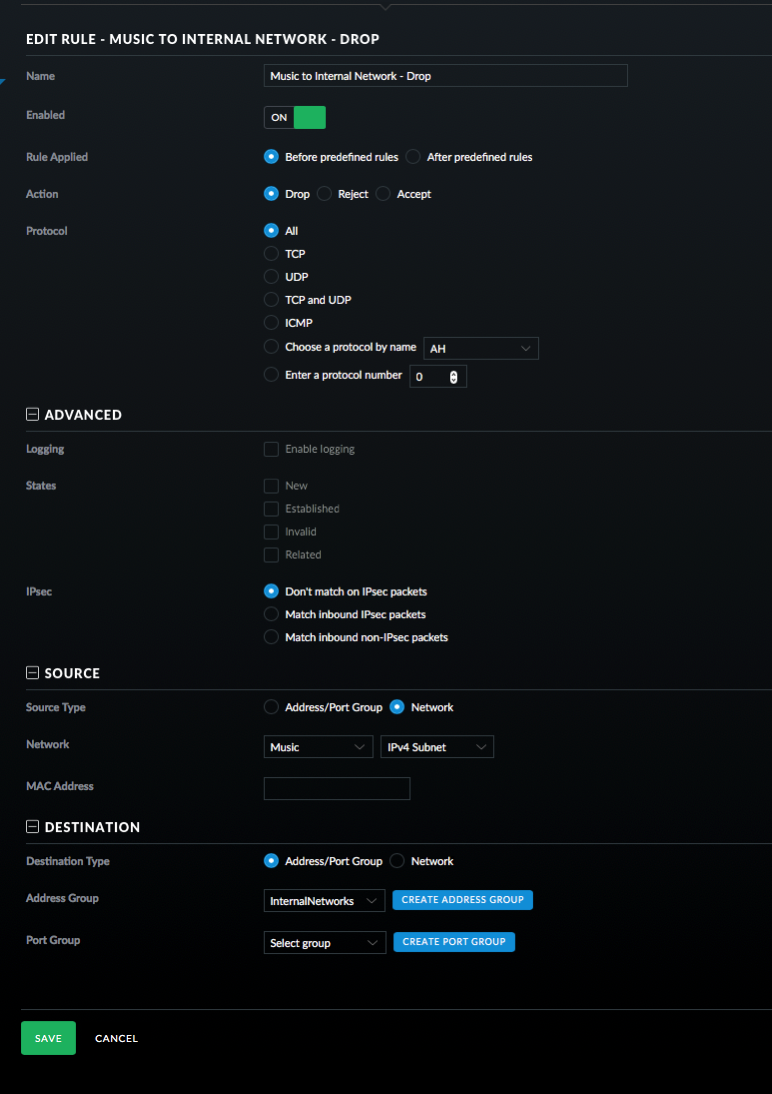
- And finally the last rule to drop all traffic from the Squeezebox to the internal network.
- On the Squeezeboxes, you have to enter the IP address of your Logitech Media Server as device discovery won’t work over subnets without some extra steps.
Still here? The process for creating rules is quite tedious, but once you get the hang of it things start moving faster. What I’ve done is restricted traffic from the Squeezebox devices so that they can only talk to the Logitech Music Server on certain ports and can only talk to the router on certain ports. I also didn’t setup rules for WAN traffic letting the Squeezeboxes talk to the Internet.
Will this fix KRACK? No. Will I be a target for KRACK? Probably not. Is isolating network traffic a good thing? Absolutely. If you have the know how to do this and a little time, I think it is worth it. I’ve gradually been moving pieces of my network to VLANs.
If there are any mistakes, please let me know! I’m not a network engineer, so it is quite possible I missed something.
Hi Scott! I’m glad you keep doing these write ups. I find them very helpful and followed many of them with my own security camera set up with ERL and Ubiquiti switch. I had a question on what to put on IOT networks to keep them off your main LAN.
If you are using items such as a logitech tv hub/remote or a lutron lighting hub. These would need to be on your main LAN to be able to connect with them to change the TV station or dim or turn on/off lights, correct? How do you differentiate what IOT device stays on the main LAN and which go on a VLAN on lock down. Thank you!
Hi Darren,
I’m glad you appreciate my posts! I write them up as a reminder of what I do in case I need to fix things in the future.
Your question about what to put on which VLAN is an interesting one. When you separate the traffic, you lose device discovery via UPnP or mDNS. There are proxies and relays to allow these to work across subnets, but that kind of defeats part of having separate subnets. What I’ve done is look at all my devices and figure out which ones require device discovery and which ones allow me to hard code an IP address. Once I’ve done this, it makes it clearer where I’ll run into trouble.
If we look at my cameras, the cameras never (or should never) connect directly to anything; my security system app connects TO them meaning that no device discovery is needed (static IP addresses are needed, though). On my IoT network I’ve put my Amazon Echos which use UPnP for discovery, a Raspberry Pi that bridges the Echos to my automation, and a few other devices that work with my automation. My main network has all the iPads, iPhones and Macs in the house. In addition, it has the Apple TV and TV tuners. While I’d like to put the Apple TV and TV tuners on a separate VLAN, AirPlay won’t work properly (I haven’t looked at ways to make it work) if the Apple TV isn’t on the same network as the iPads/iPhones. The TV tuners I could put on a separate VLAN as everything that uses them can have an IP address entered into them, but I haven’t gotten to that, yet.
So it boils down to device discovery. If devices need to discover other devices, then they basically have to be on the same VLAN or main LAN. I’m still working on my network. I hope this helps. Feel free to ask more questions!
Hi, some of the screenshots seem to be wrong? Other than that, it’s still a worthwhile read for people with squeezeboxes. Thanks