For as many years as I can remember, I’ve been the goto person for my family when they have tech problems. Anyone that is in this situation knows that this gets old pretty fast! At the beginning of January, my father started having problems with his Internet connection where he said it kept going out. I told him to call the cable company and get them to come out. He wasn’t quite convinced that it was the cable company, so he spent about a week testing out his router/access point (Apple TimeCapsule) and my sister’s router (similar device). (My dad and sister live in separate houses on the same property.)
After no real change in the stability of the connection, my dad started the game of contacting his provider. He also told me that he wanted the same router and access points that I have. Initially I said absolutely not as I didn’t want to have to walk him through configuring the UniFi devices. While the UniFi controller is pretty easy to use, it isn’t aimed at consumers. I thought about this for a day and told my dad that I’d set him up with a new router and access points on the condition that I managed all of it remotely. Once the UniFi gear is setup, there is very little management needed.
I purchased 2 UniFi UAP AC LR Access Points, a UniFi CloudKey, and a UniFi USG. I had an old Netgear PoE switch that I threw into the mix.
Setup of the pieces was pretty easy. I put all the pieces on my floor, connected them, and then hooked my MacBook Pro up to the USG to create a separate network. In addition to configuring the devices, I labeled everything and put “DO NOT UNPLUG” on the devices as power cycling seems to be a popular way to “troubleshoot” Internet connections. As I hadn’t used the CloudKey before, I was slightly confused that I had to goto the web interface of the CloudKey as well as the web interface for the USG for initial setup. I don’t remember the exact steps, but it only took a few minutes to get things running.

I setup the UniFi Controller on the CloudKey to use my UniFi login so that I could remotely manage it.
My dad and I installed the USG, switch and 1 access point next to the cable modem which took a little while to make everything look neat. The USG and the switch have those dumb slots for screws that I can never get right on the first or second try. The access point, however, has a removable base that made it a snap to install in the closet where all the equipment lives.
Once I powered everything on, it just worked as I setup the wireless networks with the same SSIDs and passwords that were already used. The only slight problem was that I had to turn off WiFi on the Time Capsules as devices were connecting to the wrong access point.
The UniFi iOS app has come a long way since Ubiquiti started it. The app now has everything I need to remotely monitor and manage the network. Ubiquiti uses a protocol for remote management that works in Chrome (on the desktop), but currently not Safari, so using the iOS app is the only way to look at the remote setup from my iPad.
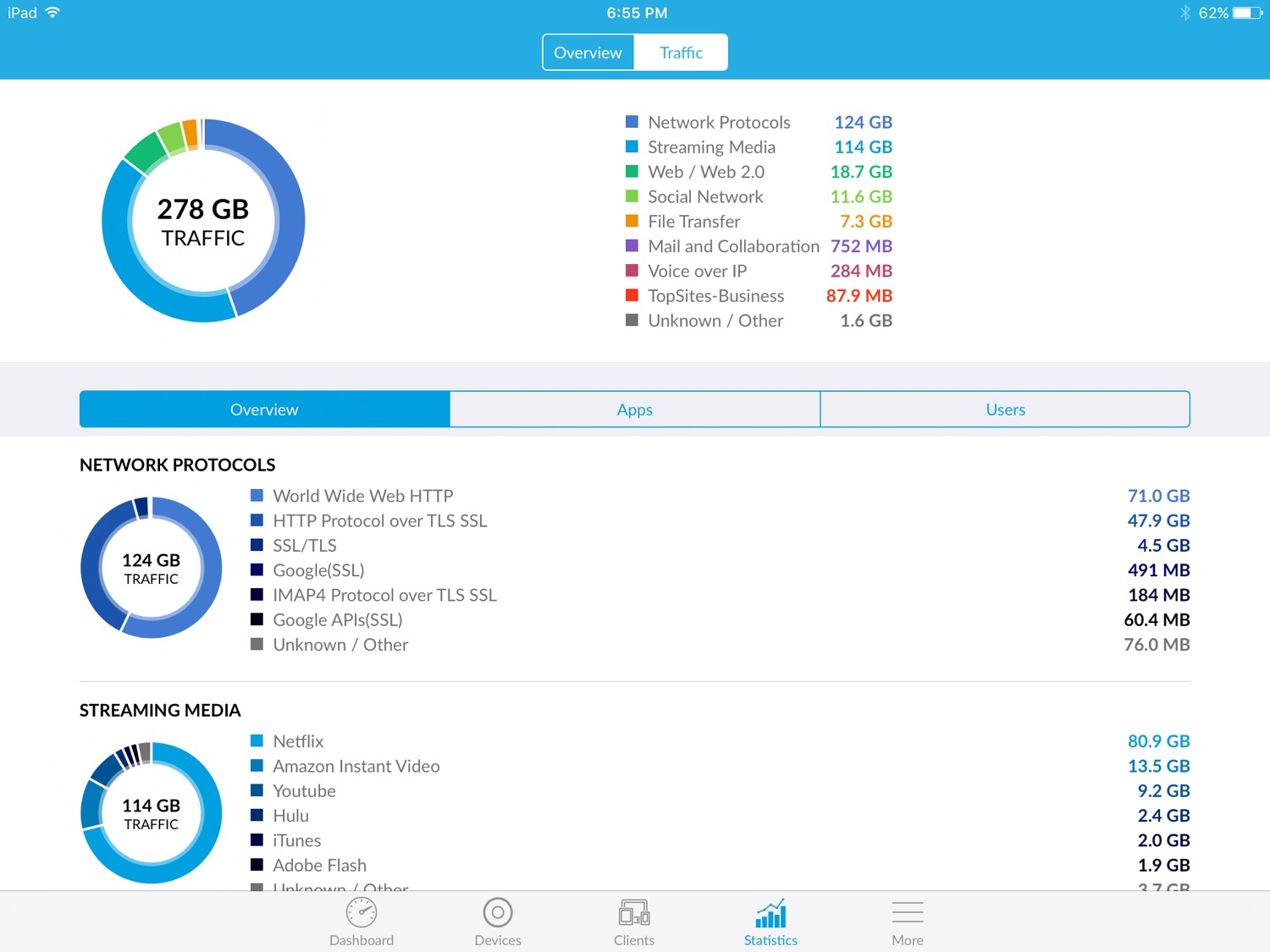
While my dad’s Internet connection has been up and down over the last 12 days, the USG and access points have been rock solid. The cable modem has been rebooted a number of times, but none of the UniFi gear has been touched.
This type of setup isn’t cheap, but it seems to be on par with some of the newer mesh systems.
Pros
- USG, CloudKey, and UAP AC LR are easy to setup for networking savvy people.
- Mobile app can handle most of the monitoring and configuration.
- UniFi Controller with the USG shows traffic statistics in pretty pictures!
- Remote access works well.
- Very stable.
- Access points provide good coverage.
Cons
- UAP AC LR uses passive 24V PoE. The PoE switch I installed is 802.3af which means that I had to use a power injector to power the access point (I could have bought an adapter from Ubiquiti to conver the 24V to 802.3af).
- Average consumer cannot easily setup the equipment.
- USG is missing some features such as GUI configuration for IPv6, static DNS entries, DHCP reservations (before device is seen on network).
- Default guest network configuration uses client isolation such that guests can’t connect to other devices on the network, but the guests can scan for other devices. I changed the configuration to use a separate VLAN and give out IP addresses in a separate range for guests. I think that this may be a better setup for an out of the box configuration when the wizard asks if you want a guest network.
- When I inserted the micro SD card into the CloudKey, it got stuck. I basically had to destroy the card to get it out. I’m not sure if this was a design issue or a manufacturing issue, but I put a new micro SD card in there and everything works fine.
Summary
While I was hesitant to set my dad up with the same networking equipment I have. I now believe that this will be the best long term strategy to supporting him. If he or my sister blame the router and access points for Internet problems, I can show them that it isn’t. Being able to remotely monitor and configure the devices (including performing upgrades) is a great benefit to anyone having to deal with someone’s Internet issues.
I hadn’t played much with the USG prior to this install as I use the EdgeRouter Lite. However, based on this and the periodic updates to the firmware and controller, I’m definitely going to be switching over to the USG in the near future (there are a few items on Ubiquiti’s roadmap that I want).
With Apple exiting the router market, people are looking for alternate solutions. If you are savvy with networking, I think the USG, UniFi Access Points, and CloudKey (unless you have an always on machine to run the controller) are a great combination. For a home setup, it may seem like a lot of money, but how much is my time worth?
Note: The USG was sent to me by Ubiquiti as a review unit. It has been sitting on my shelf for a year now simply because the controller software wasn’t exactly what I wanted at the time. The controller software has come a long way and if I had to choose between the Edge Router Lite and the USG, the USG would now be my choice.
I just wanted to let you know that I like your blog. I’m huge fan off Ubiquiti products as well. Keep up the good work.
You mentioned that you will be switching from an EdgeRouter Lite to the USG. Mind expanding on why? What will it provide that the ERL doesn’t?
I didn’t select to receive notices. Sorry for the extra post.
Hi Greg,
There are a number of reasons to switch out devices. Physically the hardware is virtually identical. The difference is in the interfaces. I like what the UniFi team is doing with the interface and the way it integrates with my UniFi switches and access points. For instance, I can setup VLANs once and have them apply to my whole network; with the ERL, I had to set them up in the UniFi controller AND the ERL. The UniFi controller has an iOS app that has come a long way in the last year allowing me to look into my network from anywhere (through the UniFi cloud).
The client management interface is more seamless; I can see all the clients across all my subnets in one view and if needed, assign static IP addresses to them, for instance.
Also, based on the roadmap that the UniFi team has outlined, I believe more of the features I want such as IPv6 will be exposed in the UI sooner than the ERL (I may be wrong here).
I’ll be including some of these items in my upcoming review of the box.
My current situation is I have an ASUS wireless router that has the wireless portion going bad. I’m turning off the wifi portion and installing a UAP Pro in the center of the house. I believe that this will cover the entire house much better than the current set up. I am planning on replacing the router portion soon, but have to wait for that a little.
I’ve just started looking at Ubiquiti and have read nothing about the USG. So that is configured through the Unifi Controller also? That might be the deciding factor for me. I’ll be setting a Raspberry Pi up as the Unifi Controller this weekend and installing the AP.
Yes, the USG is configured through the controller. You can see some of the settings for the USG in the controller even without one, but things like firewall rules, DPI, and WAN configuration can’t be seen. If your network is pretty basic, the USG may be a good bet.
Wow, that was a quick response. hehe
Yeah, it’s very basic, but won’t be for long. I’m a Linux SA and I’m trying to move into computer security, so I’ll be setting up a home lab to play around with. I will probably just create another subnet for the lab.
Hi Scott,
I wish I had read this blog before I started down the “Ubiquiti” path. I think I would have made a different choice in gear.
I bought an EdgeRouter PoE-5, 2 AC-Pros, and a CloudKey. I already owned several switches which are in several places in my house. I bought the PoE-5 becuase I thought it would be better to have the router supply the power to the AC-Pros, rather than using the supplied injectors. This, I now conclude was not my best solution. The PoE-5 really only has 3 ports in a single VLAN, so two are used for the AC-Pros, and the third goes to a Cisco switch. The CloudKey is plugged into the Cisco switch and uses a power injector, which is NOT supplied with the device.
I have a two story, 3600 square foot house and I love the fact that I can have my AC-Pros in different parts of the attic and not have to worry about power since there isn’t any power in my attic. (More of multiple crawl spaces than an attic!)
I am not a network engineer and I found it a little frustrating getting everything working the way I wanted. Ubiquiti gear is not for the faint of heart. You need some technical ability otherwise, IMHO, you should stay away from the stuff. Fortunately, the Ubiquiti “chat” folks are very knowledgable and helped me through my issues.
But getting back to my reason for commenting – since I already owned a decent gig switch, I think that I should have purchased the USG, and used the power injectors with short cables between the injectors and the switch. So my configuration would have looked very much like your picture.
Would it be stupid to now put a USG in front of the PoE-5, or even replace the PoE-5 with a USG? Money isn’t really an issue here – it’s accessibility and configuration capabilities plus the monitoring.
And how are you accessing the USG and CloudKey remotely? I can access my CloudKey only when on the home network. I can manage the PoE-5 remotely – that was easy to setup. But when I am away from the house, I am unable to see the CloudKey. I suspect I need to modify the config in my PoE-5 but I am not sure what needs to be done to allow remote access to my CloudKey.
Cheers.
Hi Andy,
As for accessing the CloudKey remotely, turn on Cloud Access in the controller. I don’t believe you need to do any port forwarding in the PoE-5.
I wouldn’t put the USG in front of the PoE-5 as that is more of a configuration nightmare! Should you replace the PoE-5 with a USG? See my review of the USG. I replaced my EdgeRouter Lite with a USG. I’m pleased with the decision, but it required a bit of work.
Wow – thanks for the quick reply!
Cloud Access is turned on. What I think may be my issue is the name and how it is found. When I am on my local network, my Cloud Key shows up with its default name “Unifi CloudKey” and its local IP. But what I believe is my remote name, shows up as “disconnected”. I think I am missing a step where I correctly use my home DNS name to find the CloudKey. Not sure if I am making sense here. But when you are on your home network, do you see the “external” name for you CloudKey and if so, what configuration update did you make to see it? It is possible that the USG hides this particular mess from other routers.
Thanks,
Andy.
When I had the ERL, I didn’t do anything special and believe that I was able to access my controller remotely. You don’t need to use DNS to find the CloudKey. I’d ask the UniFi support folks for assistance. I know that I didn’t setup port forwarding. I’m not exactly sure how it works.
Hi Scott,
OK, my CloudKey is now accessible outside my network. But the external name shows as “Offline”. Ubiquiti support says this happens if you install a local controller on a PC first, then uninstall it when you add a CloudKey, which is exactly what I did.
So when outside my network, I log into “unifi.ubnt.com” and click on my local CloudKey entry and then select “Launch Using Hostname”. It’s just not very intuitive. (Obviously, the hostname must resolve via DNS to the IP of your router.)
So my recommendation to anyone reading this thread – “if you are going to want access outside your network, buy a CloudKey when you purchase the APs and do not install the local Unifi client on a PC”.